In 2020, Intel introduced the open-source Data Plane Development Kit (DPDK) framework to address packet performance issues in computing-intensive environments. Managed by the Linux Foundation, the framework aims to optimize data paths used to execute packet processing on multiple core CPUs. It achieves this by using a number of techniques such as the DMA access mode, a polling system instead of interrupts, SSE for massive data copying, Huge Pages for faster virtual to physical page conversions, thread affinity for better cache utilization, lock-free user-space multi-core synchronization using rings and NUMA awareness. Still mostly deployed on Intel and AMD x86 processors, DPDK is also available on ARM processors, such as BlueField, DPAA and Octeon as well as PPC processors, such as POWER1. DPDK enables developers to build their own packet forwarding applications, such as virtual routers and switches.
Understanding the packet journey
To understand how DPDK improves application performance, it is important to understand the role of network interface cards (NICs). A NIC connects the computer to Wi-Fi or Ethernet, and acts as an intermediary for incoming and outgoing packets. It executes a range of functions such as translating data into digital signals, executing I/O interrupts, detecting transmission errors and providing direct memory access.
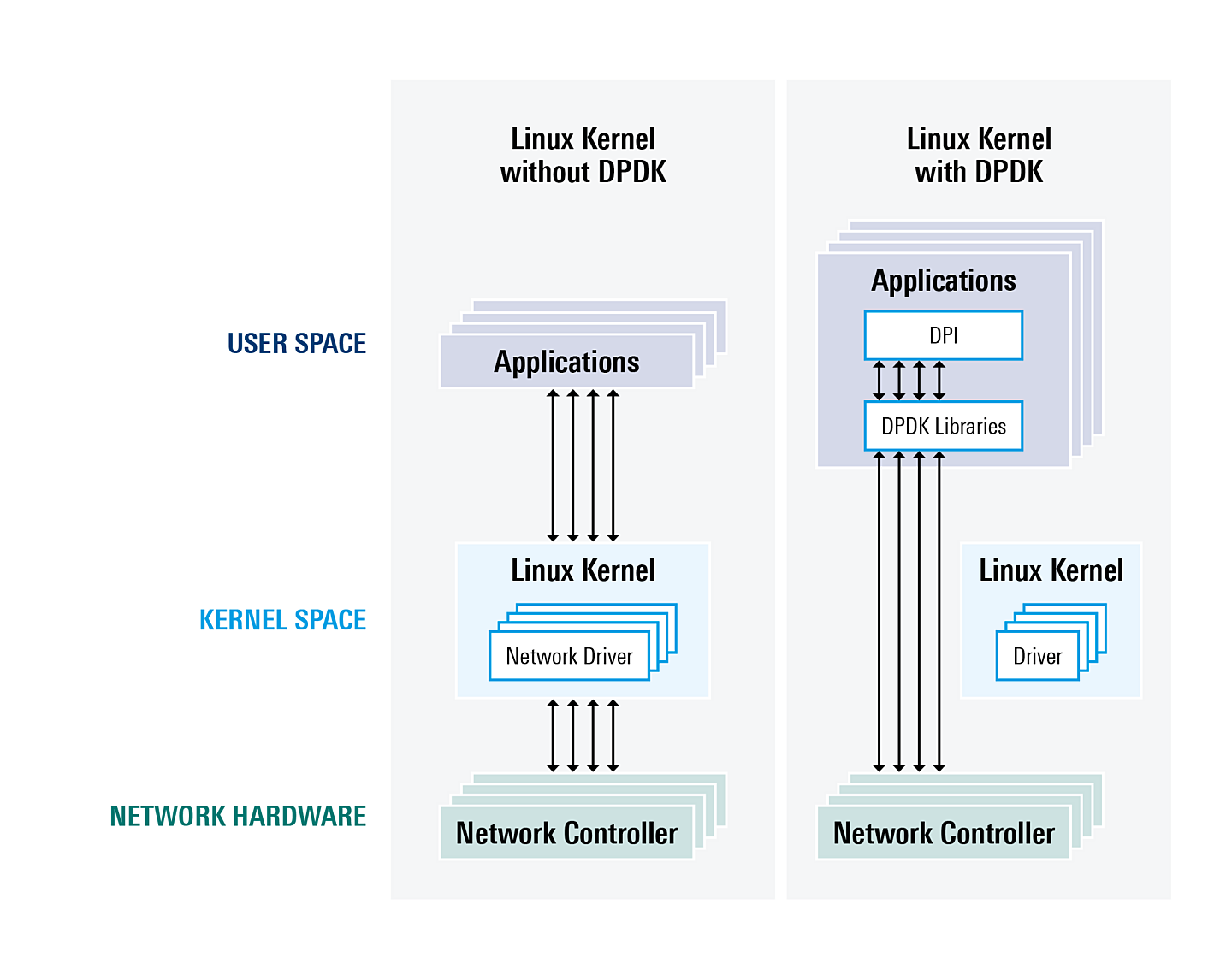
In standard settings, a NIC is managed by the OS kernel. To initiate packet processing, a NIC generates CPU interrupts based on the interrupt moderation specifications, for example, maximum packets or time-outs. Packets are then copied out from the NIC to the kernel buffer queue, and then copied out to the user space, where these packets are processed by the respective application.
OS kernel bypass
DPDK on the other hand, bypasses the OS kernel, leveraging a set of libraries and a poll mode driver (PMD). Using APIs, DPDK’s PMD programs one or more cores to actively look for packets and fetch them as soon as they appear in the packet I/O path. DPDK pushes these packets to the application layer, enabling processing to begin as soon as a packet arrives. Using the interface provided by DPDK libraries, users access the NIC port and execute packet processing from the user space.
By circumventing various rounds of copying and by making packet buffers (DPDK mbufs) directly available in the user space, DPDK allows DPDK-based applications, such as a NGFW or an EPC, to expedite packet processing. In combination with other DPDK techniques, such as the DMA access mode, Huge Pages, NUMA awareness and a lock-free buffer queue, DPDK significantly improves the speed by which these applications execute their functionalities. It thus contributes to enhanced network throughputs, speeds and latencies.
DPDK is critical for applications deployed in heavy-compute environments like the cloud. It enables networking applications, such as NGFWs, EPC, 5G UPFs, SD-WAN/SASE, IP probes and IDS/IPS to expand their processing capacity and improve their outputs. Benefitting both virtualized and cloud-native environments, DPDK enhances the capacity of VNFs and CNFs to manage high traffic volumes and handle latency-sensitive applications.
Accelerating DPDK with deep packet inspection
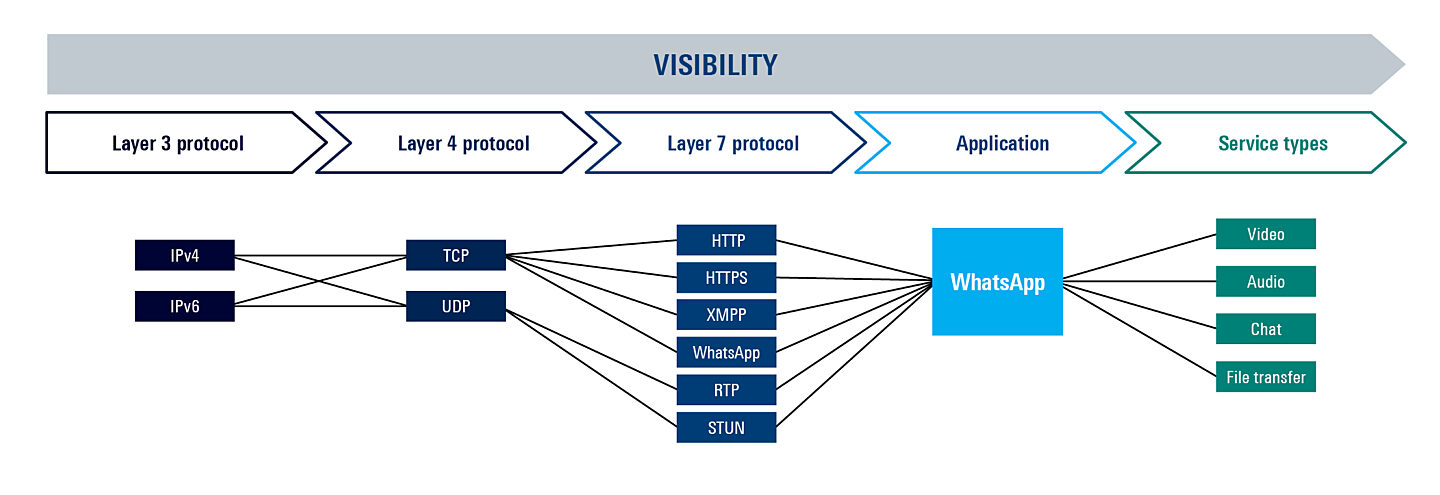
ipoque’s deep packet inspection (DPI) software, R&S®PACE 2, is optimized to deliver the best performance within a DPDK environment. With various integration examples that demonstrate the analysis of mbufs within different DPDK utilities, users can seamlessly integrate the DPI engine R&S®PACE 2 within any DPDK-application that requires real-time traffic awareness. The integration allows applications to rapidly scale their traffic filtering and forwarding capacity while eliminating the risk of latencies often associated with a separate stream of packet inspection.
By integrating R&S®PACE 2, applications benefit from its cutting-edge traffic classification techniques which include statistical, behavioral and heuristic analyses, advanced machine learning and deep learning techniques. Using DPI’s traffic analysis, applications can draw real-time information on a wide range of attributes – including protocols, applications and services – using an extensive, weekly updated signature library. R&S®PACE 2 also delivers real-time threat intelligence, enabling applications to detect traffic that is malicious, anomalous or suspicious.